Define Buffer Overflow In Network Security
 Buffer Overflow Format String Attacks The Basics Infosec Resources
Buffer Overflow Format String Attacks The Basics Infosec Resources

 What Is Buffer Overflow Definition From Whatis Com
What Is Buffer Overflow Definition From Whatis Com
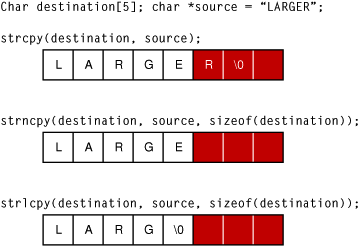 Avoiding Buffer Overflows And Underflows
Avoiding Buffer Overflows And Underflows
 Most Common Cyber Vulnerabilities Part 2 Buffer Overflow
Most Common Cyber Vulnerabilities Part 2 Buffer Overflow
 Interactive Guide To Buffer Overflow Exploitation Exploitation Interactive Overflowing
Interactive Guide To Buffer Overflow Exploitation Exploitation Interactive Overflowing
 April 2015 Question Paper Bscit Question Papers Bscit Semester V Question Paper Network Security This Or That Questions Question Paper Old Question Papers
April 2015 Question Paper Bscit Question Papers Bscit Semester V Question Paper Network Security This Or That Questions Question Paper Old Question Papers
 Infographic How Botnets Work To Attack Networks Cyber Attack Cyber Threat Networking
Infographic How Botnets Work To Attack Networks Cyber Attack Cyber Threat Networking
 Buffer Overflow Attack Defense Infosec Resources
Buffer Overflow Attack Defense Infosec Resources
 Terms Used In Field Of Hacking Cyber Security Cybersecurity Training Hacks
Terms Used In Field Of Hacking Cyber Security Cybersecurity Training Hacks

 Protobuf Inspector Is A Simple Program That Can Parse Google Protobuf Https Developers Google Com Protocol Buffers Enc Computer Security Definitions Buffers
Protobuf Inspector Is A Simple Program That Can Parse Google Protobuf Https Developers Google Com Protocol Buffers Enc Computer Security Definitions Buffers
 Powermemory V1 4 Exploit The Credentials Present In Files And Memory Credentials Security Tools Memories
Powermemory V1 4 Exploit The Credentials Present In Files And Memory Credentials Security Tools Memories
 Buffer Overflow Attacks Explained With Examples
Buffer Overflow Attacks Explained With Examples
 Cissp Certification Traning Tip Types Of Attackts For More Information To G C In 2020 Cyber Security Certifications Cyber Security Course Computer Security
Cissp Certification Traning Tip Types Of Attackts For More Information To G C In 2020 Cyber Security Certifications Cyber Security Course Computer Security
 What Is Stack Based Buffer Overflow Hackersonlineclub
What Is Stack Based Buffer Overflow Hackersonlineclub
 Cissp Training Exam Tip Exams Tips Computer Learning Cyber Security Certifications
Cissp Training Exam Tip Exams Tips Computer Learning Cyber Security Certifications
 An Introduction Of Sql Injection Buffer Overflow Wireless Attack
An Introduction Of Sql Injection Buffer Overflow Wireless Attack
 How Buffer Overflow Attacks Work Netsparker
How Buffer Overflow Attacks Work Netsparker
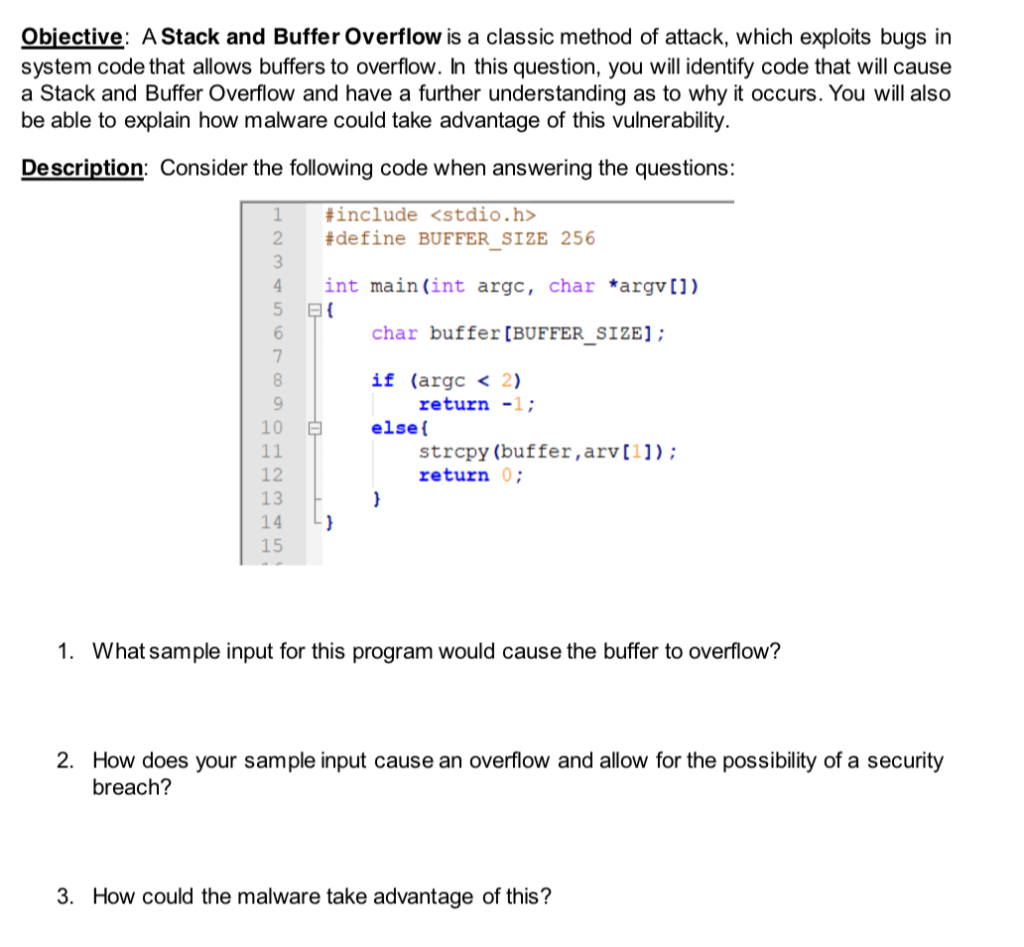 Obiective A Stack And Buffer Overflow Is A Classi Chegg Com
Obiective A Stack And Buffer Overflow Is A Classi Chegg Com
